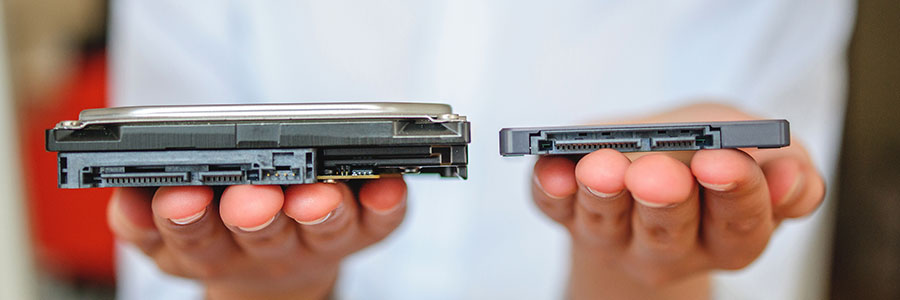
Intel has released a totally new type of hard drive designed for faster boot times and storage. People in the market for a new hard drive may consider this technology, but before making any big investments, you need to know the full capabilities of Optane SSD. Below is our review of Intel’s newest storage device.
Blog
No Ransom: a place for free decryption
OMS: The best way to organize online sales
Why your business needs a hardware firewall

Cybersecurity is one of the final bastions of hardware superiority. More and more IT solutions are being hosted in the cloud, and business owners are being told that software is all they need to get the job done, which is half true. When it comes to perimeter security you definitely need a hardware firewall, with a little something extra.
Utilize Snapchat for business growth

Businesses nowadays are focusing their marketing efforts towards social media. Precious time and money are being invested in expanding customer base, establish corporate identity, and drive revenue. That’s why it’s vital for owners to know which platforms work, and which ones don’t. And this is no walk in the park.
Fileless malware: who are the targets?
Real-world audits: disaster recovery plans
Social media platforms that suit your SMB
Popular printer brands are prone to attacks
5 great ways to prevent cyber-attacks
As technology consultants, we’re stuck between a rock and a hard place. We want to provide our clients with enterprise-level IT, but that requires that we specialize in overwhelmingly intricate technology. Explaining even the most foundational aspects of our cyber-security would most likely put you to sleep before convincing you of our expertise.